Global Capability Centers (GCCs) are no longer back-office processing centers; they are strategic innovation engines that deal with mission-critical product development, data science, and platform engineering. There are over 1,900 GCCs in India, which have earned approximately 65 billion and have an employment of about 1.9 million professionals, which is a large scale that makes the issue of GCC security an economic and operational issue of concern. Traditional network boundaries have been erased by the GCC work scale and sensitivity, alongside migration to the cloud, hybrid work, and API-driven operations. At the same time, threat actors have now become more tactical: ransomware, data exfiltration, and compromise of supply chains now target distributed teams and third-party services as opposed to just one data center. These two forces have generated a need for a new security posture: Zero-Trust Architecture (ZTA).
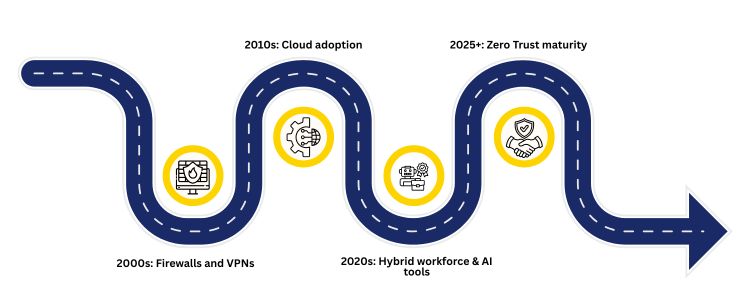
The first GCC security measures, such as perimeter firewalls, VPNs, and trusted internal networks, mirrored enterprise IT at the time. That model was enough in cases where the majority of workloads were on-premise and access was office-bound. When GCCs were turned into cloud-native hubs (microservices, DevOps pipelines, and external data feeds), the trusted inside/untrusted outside assumption started to collapse, lead times of breach detection became longer, and horizontal movement and insider risk increased. As a result, perimeter defense was no longer adequate and was now required. Why Zero Trust Is The Next Best Thing Zero Trust does not count on presumed trust but refers to the verification of trust: never trust, always verify. The new GCC’s business realities are global workforces, temporary computing, and more precise data access requirements that are directly related to its core tenets of identity as the new perimeter, least privilege, micro-segmentation, and continuous monitoring. The market momentum indicates the same trend: According to industry surveys and analysts, Zero Trust is shifting faster and faster, and most organisations actively pursue or consider Zero Trust programs in 2024-2025.
The following is a succinct perspective of the transformation underway of GCC security controls towards the Zero-Trust practices.
It is not a security game to go zero trust; rather, it is an economic enabler for the GCC and parent organizations. Recent studies and market forecasts indicate that there is strong business momentum currently supporting these architectures as vendors and businesses increase their investments in Zero-Trust toolkits. Organisational And Human Changes It is not just a technology that will provide resilient GCC security. Leaders should invest in three related areas, namely: (1) Talent – Establish cybersecurity Centres of Excellence within GCCs and train engineers in secure coding and cloud hardening; (2) Process – Introduce security gates into CI/CD and procurement; and (3) Culture—Make verifying continuously the responsibility of product, data, and business teams. GCCs that position Zero Trust as a program (people + process + tech) instead of a product have a higher payback faster and more sustainably.
The three years to come will witness Banking GCCs as key constructionists of two long-term trends: Open Finance is not a product but rather an operating model; the operating muscle is provided by GCCs. With GCCs taking on more engineering, risk, and product responsibilities, banks can become more competitive with fintech-native platforms without losing the trust of customers and regulators.
There are several trends that are expected to increase into 2026, including extensive migration of the existing VPNs to identity-based access, ubiquitous JIT provisioning, and more use of AI to detect and respond to threats. GCCs should be vigilant because attackers will continue to target weak points, such as unmanageable endpoints at Tier-2/3 locations, poorly managed cloud identities, and third-party vendors. The urgency is highlighted by recent national and industry reports: the landscape of cyber threats in India was registered in significant amounts of malware and targeted ransomware incidences in cities and industries, which supports the necessity of contemporary architectures and prompt detection. Conclusion The direction of GCC security is evident: perimeter defense brings stability; Zero Trust provides resilience and a competitive edge. This will become a necessity rather than a pleasant surprise in case GCCs continue to perform their strategic duty, which is to provide innovation at scale, safeguard customer trust, and conduct global operations. Chief executive officers who focus on identity, visibility, and least privilege today will open the door to reduced risk, regulatory certainty, and increased rates of economic payoff throughout their GCC presence.
A GCC is an offshore facility of a multinational company that undertakes niche roles such as research and development, information technology service and strategic management. It is a government program that gives the women entrepreneurs up to 1 crore in bank loans to fund greenfield projects. Personal responsibilities and unconscious bias are the factors that lead to their mid-career attrition and slow them down in their careers. They introduce new ideas, understanding, and team-oriented leadership that speeds up the advancement of such areas as AI and cybersecurity. By 2030, women are expected to take up 25-30 per cent of GCC leadership positions, which will be paramount to the growth of the Indian market. Aditi, with a strong background in forensic science and biotechnology, brings an innovative scientific perspective to her work. Her expertise spans research, analytics, and strategic advisory in consulting and GCC environments. She has published numerous research papers and articles. A versatile writer in both technical and creative domains, Aditi excels at translating complex subjects into compelling insights. Which she aligns seamlessly with consulting, advisory domain, and GCC operations. Her ability to bridge science, business, and storytelling positions her as a strategic thinker who can drive data-informed decision-making.
A Brief History
Transformations in the GCCs
Security Area
Old Way (Perimeter Defence)
New Way (Zero-Trust Approach)
Access Control
Any person within the office system was automatically trusted.
No access can be granted without verifying every user and device.
User Permissions
Wide access is provided to teams or positions.
The access given is restricted in time and purpose.
Network Security
Lined by firewalls and solid boundaries.
Separated into smaller areas in order to prevent the spread of one violation.
Monitoring
Audited occasionally.
Monitored with real-time warning and data analysis.
Data Protection
Data encryption was done on storage alone.
Data protection is provided during storage, sharing and use
Governance
Departments handled policies independently.
Core policies are used in all the GCC destinations.
Economic Advantages
Future Perspective
New Trends And Short-Term Prospects
frequently asked questions (FAQs)

Aditi
Hey, like this? Why not share it with a buddy?
Related Posts
Recent Blog / Post
- Pharma GCC Setup Services in India: Strategic Considerations for CXOs January 9, 2026
- Why Enterprises Are Rethinking Their GCC Strategies in 2026 January 8, 2026
- Why Most Enterprise Expansion Strategies Fall Short of Projections, And How a GCC Enabler Can Bridge the Gap January 7, 2026
- India’s GCC Ecosystem: Why the World’s Biggest Companies Are Betting Their Future on it January 3, 2026
- Healthcare GCCs in India: Where the World’s Pharmaceutical Innovation Actually Happens January 2, 2026
- Circular Economy Models and Their Relevance to Manufacturing GCCs December 30, 2025
- GCCs in Agritech: Digitizing Global Food Security December 29, 2025
- Renewable Energy GCCs: Accelerating Global Green-Tech Development December 29, 2025
- Cyber Resilience 2030: Multi-Layer Security Architecture for GCCs December 26, 2025
- Building an Integrated Risk Management Framework for Multi-Region GCCs December 26, 2025
- The Ethics of Automation: How GCCs Maintain Human Oversight in AI Workflows December 25, 2025
- Future of HR in GCCs: Data-Led, Skills-Based, and GenAI-Driven December 25, 2025
- The Proposal to Standardize India’s GCCs for Unshakeable Global Leadership December 24, 2025
- Global Capability Centers: A Strategic Growth Model for B2B Enterprises December 24, 2025
- AI Ethics & Compliance Mandates for GCC Operations in 2025 December 23, 2025