In 2025, the global cyber threat landscape is more dangerous than ever. Cyber criminals are using advanced techniques such as AI and deepfake to carry out targeted attacks, while companies are facing increasing pressure to ensure the safety and uninterrupted global operation of sensitive data. The Global Capability Center (GCC), also known as global captive centers, has overtaken its traditional role of cost-saving units. Today, they are the leading promoters of innovation, digital change, and now, cybersecurity. As nerve centers for multinational enterprises, GCC should adopt top-level cybersecurity strategies to be flexible, tight, and compliant. In this blog, we find out why cybersecurity is important for the GCC in 2025 and how the Indo-based Global Innovation Center is moving forward to face this challenge.
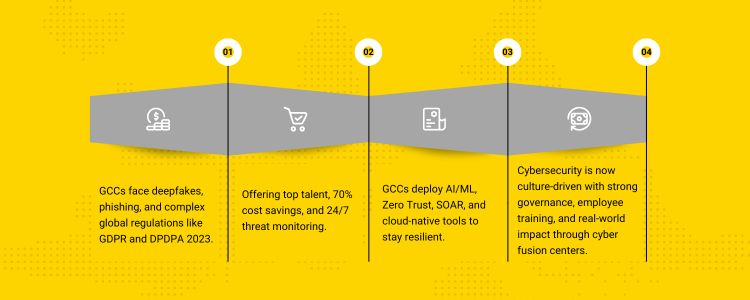
Cyber threats in 2025 are increasing not only in quantity but also in complexity:
In 2025, GCC is developing as strategic cybersecurity centers in India, which provide many benefits: 24/7 Monitoring: Follow-the-sun models allow round-the-clock threat monitoring and faster incident response.
GCC is taking advantage of emerging technology to create a strong defense system. Safety Automation (SOAR): Automate regular safety work for fast response and better efficiency.
Cybersecurity is not only about technology; It is also about people, policies, and preparations.
The benefits of strong cybersecurity in GCC operations are measurable and important: Data violations and downtime decrease A global financial firm created a cyber fusion center in its GCC in India. This COE used AI and 24/7 monitoring to prevent ransomware attacks, protect customer data, and maintain confidence. Future approach: GCC no longer supports centers. They are the global innovation center, which actively secures and enables the digital future of their original organizations.
In 2025, the cybersecurity landscape is more complex, and the role of global capacity centers has never been so important before. With special talent, cost-effective measurement, and access to state-of-the-art technology, GCCs in India are emerging as a new stronghold of cybersecurity. From creating a Zero Trust Framework to AI-operated threats, India-based GCCs are able to secure and scale global operations for some of the largest companies in the world.
Do you want to build or strengthen your GCC cybersecurity capabilities? Participate with Inductus Global, who understand the complications of safe digital operations. Let us help you to create a flexible GCC, ready for the future in India, which not only supports your global business but also protects it.
They establish privacy and compliance Center for Excellence (COE), GDPR, and DPDPA of India. 2023, ISO 27001 and NIST Align with global standards such as structures, and maintain rigid audit trails. “Zero Trust” means “Never trust, always verify.” This model is used to limit access, apply least privilege principles, and divide the network, which is important for modern cybersecurity strategies. Through regular staff training, phishing simulation, real-time awareness programmes, and governance policies, GCC is involving daily work in cybersecurity culture. In companies with mature cybersecurity, fast enterprise response time, high customer confidence, and better visibility in the IT and OT environment. Partnering with a consulting firm or GCC service provider can help assess current gaps, design the GCC operating model, hire skilled cybersecurity talent, and implement best-in-class tools and compliance frameworks Aditi, with a strong background in forensic science and biotechnology, brings an innovative scientific perspective to her work. Her expertise spans research, analytics, and strategic advisory in consulting and GCC environments. She has published numerous research papers and articles. A versatile writer in both technical and creative domains, Aditi excels at translating complex subjects into compelling insights. Which she aligns seamlessly with consulting, advisory domain, and GCC operations. Her ability to bridge science, business, and storytelling positions her as a strategic thinker who can drive data-informed decision-making.
Intense Landscape of Cyber Threats in 2025
GCC as Strategic Cyber Security Powerhouse
Emerging Technologies that Increase Cybersecurity
Building the Culture of Security and Strong Governance
Impact on the Real World and the Path Ahead
Conclusion
frequently asked questions (FAQs)

Aditi
Hey, like this? Why not share it with a buddy?
Related Posts
Recent Blog / Post
- The Role of GCCs in Accelerating Corporate R&D and IP Creation November 4, 2025
- Navigating Geopolitical Risks: A Guide for GCC Leaders November 4, 2025
- Why Mid-Sized Companies are Embracing the GCC Model October 16, 2025
- What Is A Global Capability Center (GCC), and Why Is It Essential For Modern Business? October 16, 2025
- Gurugram’s Tech Ascent: Decoding the New Haryana GCC Policy October 15, 2025
- Scaling Your Tech Team: A Beginner’s Look at the Offshore Development Center October 15, 2025
- Agile Methodologies for GCCs: A Blueprint for Success October 6, 2025
- The Legal and Compliance Checklist for a New GCC Setup October 4, 2025
- The Rise of Niche GCCs: A Focus on Specialised Capabilities October 4, 2025
- The Impact of Regulatory Changes on GCC Operations October 4, 2025
- Cybersecurity for GCCs: A Proactive Approach to Data Protection September 30, 2025
- Beyond Cost: Measuring the True ROI of Your GCC Investment September 29, 2025
- The Future of GCCs in the Retail Sector: A Strategic Playbook September 29, 2025
- David vs Goliath: Mid-Sized GCCs Quietly Outperform the Big Brands September 29, 2025
- Infineon’s Big Bet on India: Inside Its First GCC in GIFT City September 29, 2025
















